1. Introduction & Overview
What is a Private Key?
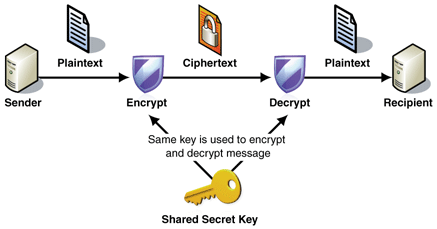
A private key is a secret alphanumeric string used in cryptography to:
- Sign transactions
- Prove ownership of digital assets
- Generate public keys
It is the core security component in cryptoblockcoins and blockchain systems. Without a private key, you cannot spend or control the associated cryptocurrencies.
Example (Bitcoin Private Key):
5HueCGU8rMjxEXxiPuD5BDuYk1wZy5kFeRzN2rP9j6b9tJ7C
Key points:
- Private keys must be kept confidential
- Loss of a private key means loss of access to assets
- It is mathematically linked to a public key through elliptic curve cryptography (ECC)
History / Background
- Private keys emerged with public key cryptography, introduced by Whitfield Diffie and Martin Hellman in 1976.
- Satoshi Nakamoto’s Bitcoin whitepaper (2008) formalized the use of private keys for securing digital money.
- Today, all major blockchains (Ethereum, Bitcoin, Solana, Cardano) rely on private keys for transaction authorization.
Relevance in Cryptoblockcoins
- Essential for transaction signing: ensures the authenticity of transactions.
- Controls access to wallets and digital assets.
- Enables identity verification in decentralized systems without a central authority.
2. Core Concepts & Terminology
| Term | Definition | Relevance |
|---|---|---|
| Private Key | Secret alphanumeric code controlling access to funds | Must remain confidential |
| Public Key | Derived from private key using ECC | Used to receive funds and verify signatures |
| Wallet Address | Hash of public key | Used as a destination for sending/receiving funds |
| Digital Signature | Cryptographic proof of ownership | Validates transactions |
| Seed Phrase | Human-readable representation of private key(s) | Used for backup and recovery |
Lifecycle in Cryptoblockcoins:
- Generate private key → 2. Derive public key → 3. Generate wallet address → 4. Sign transactions → 5. Broadcast to blockchain → 6. Verified by network → 7. Asset transfer confirmed
3. Architecture & How It Works
Components & Workflow
- Key Generation Module: Creates private/public key pairs using ECC or EdDSA algorithms.
- Wallet Interface: Stores private keys securely (hot or cold wallets).
- Transaction Signer: Signs transactions using the private key.
- Blockchain Network: Validates signed transactions using the corresponding public key.
Step-by-Step Workflow:
- User generates a private key.
- Wallet software derives the public key.
- Wallet creates a wallet address from the public key.
- When sending crypto:
- Wallet signs transaction with private key.
- Transaction broadcasted to blockchain.
- Miners/nodes verify signature using public key.
- If valid, transaction added to blockchain.
Architecture Diagram Description (Text-Based)
+-------------------+
| User / Wallet |
+-------------------+
|
v
+-------------------+ Generate key pair
| Key Generation | -----------------+
+-------------------+ |
| v
v +----------------+
+-------------------+ | Public Key & |
| Private Key Store | <--------| Wallet Address |
+-------------------+ +----------------+
|
v
+-------------------+
| Transaction Signer|
+-------------------+
|
v
+-------------------+
| Blockchain Network|
+-------------------+
Integration Points with CI/CD or Cloud Tools:
- Cloud Wallets / APIs: Can integrate key management with secure cloud services like AWS KMS, Azure Key Vault.
- CI/CD pipelines: Automated deployments using encrypted private keys for signing smart contracts or NFTs.
4. Installation & Getting Started
Prerequisites
- Python or Node.js environment
- Knowledge of ECC cryptography
- Wallet software (Electrum, MetaMask)
- Optional: Hardware wallet (Ledger, Trezor)
Hands-On: Generating a Private Key (Python Example)
from ecdsa import SigningKey, SECP256k1
# Generate a new private key
private_key = SigningKey.generate(curve=SECP256k1)
print("Private Key (hex):", private_key.to_string().hex())
# Derive the public key
public_key = private_key.get_verifying_key()
print("Public Key (hex):", public_key.to_string().hex())
Node.js (bitcoinjs-lib)
const bitcoin = require('bitcoinjs-lib');
// Generate random key pair
const keyPair = bitcoin.ECPair.makeRandom();
console.log("Private Key (WIF):", keyPair.toWIF());
console.log("Public Key:", keyPair.publicKey.toString('hex'));
Key Notes:
- Do not hardcode private keys in production code.
- Use encrypted storage or hardware wallets.
5. Real-World Use Cases
| Use Case | Blockchain | Description |
|---|---|---|
| Transaction Signing | Bitcoin, Ethereum | Every transaction is signed with a private key to authorize spending |
| Smart Contract Deployment | Ethereum | Private key signs contract deployment transactions |
| NFT Minting | Solana, Ethereum | Private key authorizes creation and transfer of NFTs |
| Cold Storage Backup | Any blockchain | Seed phrases derived from private keys are stored offline for security |
Industry Examples:
- Exchanges (Coinbase, Binance) use private keys for hot and cold wallet management.
- Decentralized apps (DeFi platforms) require private keys for user authorization.
- NFT marketplaces use private keys for minting and transferring digital collectibles.
6. Benefits & Limitations
Key Advantages
- Full control over assets.
- High-security standard using ECC.
- Enables decentralized trustless systems.
Common Challenges / Limitations
- Loss = irreversible asset loss.
- Private key theft = complete compromise.
- Managing multiple keys can be cumbersome.
Comparison Table: Private Key vs. Alternative Security Approaches
| Feature | Private Key | Custodial Wallet | Multi-Sig Wallet |
|---|---|---|---|
| Control | User only | Provider | Shared |
| Security | High | Moderate | High |
| Recovery | Only via seed phrase | Provider | Multiple users |
| Use Case | Personal wallet | Exchange account | Large funds / institutions |
7. Best Practices & Recommendations
Security Tips
- Never share your private key.
- Use hardware wallets for high-value crypto.
- Encrypt backups and store offline.
- Regularly rotate keys for enterprise use.
Performance & Maintenance
- Monitor wallet software for updates.
- Use multi-sig for large enterprise funds.
- Conduct periodic audits.
Compliance & Automation
- Implement KMS for enterprise key management.
- Automate transaction signing in CI/CD securely using environment variables.
8. Comparison with Alternatives
| Alternative | Pros | Cons |
|---|---|---|
| Custodial Wallet | Easy for beginners | Provider controls funds |
| Multi-Signature | Increased security | Requires multiple approvals |
| Smart Contract Wallets | Automation & programmable | Complexity, gas fees |
When to choose a Private Key over others:
- You want full ownership of assets.
- You require decentralized security.
- You have knowledge of safe key management.
9. Conclusion
- Private keys are the cornerstone of blockchain security.
- Proper management ensures asset safety, transaction integrity, and user autonomy.
- Future trends include:
- Threshold cryptography
- Hardware wallet innovations
- Decentralized key recovery mechanisms
Official Docs and Communities:
- Bitcoin Developer Guide – Keys
- Ethereum Documentation – Accounts & Keys
- Bitcoin StackExchange
- Crypto Wallet Security Best Practices – Ledger
Category: