1. Introduction & Overview
What is a Digital Signature?
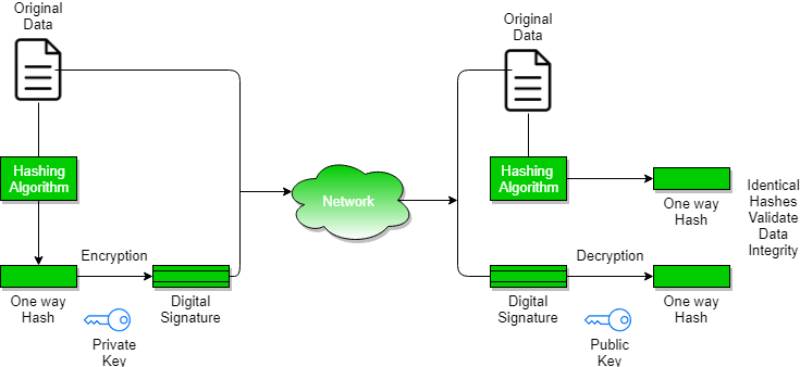
A digital signature is a cryptographic technique used to ensure:
- Authentication: Verifying the identity of the sender.
- Integrity: Ensuring the message or transaction has not been altered.
- Non-repudiation: The sender cannot deny the action.
In simpler terms, it’s like a digital fingerprint of data, uniquely generated using the sender’s private key.
History & Background
- 1976: Whitfield Diffie and Martin Hellman introduced the concept of public-key cryptography.
- 1977: Ronald Rivest, Adi Shamir, and Len Adleman (RSA) created the first widely-used digital signature algorithm.
- 1990s: Digital signatures became standard in securing electronic communications and transactions.
- 2010 onwards: Used in cryptocurrencies like Bitcoin to secure peer-to-peer transactions without a central authority.
Relevance in Cryptoblockcoins
In blockchain and cryptoblockcoins:
- Every transaction must be signed digitally to prevent fraud.
- Ensures only the owner of a cryptocurrency can spend their coins.
- Provides trustless verification, eliminating the need for intermediaries.
2. Core Concepts & Terminology
| Term | Definition | Relevance in Cryptoblockcoins |
|---|---|---|
| Private Key | Secret key held by the owner | Used to generate the digital signature |
| Public Key | Publicly shared key corresponding to private key | Used by nodes to verify digital signatures |
| Hash Function | One-way function generating a fixed-size output from input | Ensures integrity of transaction data |
| Signature Verification | Process of checking validity of signature | Confirms authenticity of the sender and data |
| Nonce | Arbitrary number used once in cryptography | Prevents replay attacks |
Lifecycle Fit in Cryptoblockcoins:
- User initiates a transaction.
- Transaction data is hashed.
- Digital signature is created using the private key.
- Signature and transaction data are broadcast to the network.
- Nodes verify using the sender’s public key.
- If valid, transaction is added to the blockchain.
3. Architecture & How It Works
Components of Digital Signature in Blockchain
- User Wallet: Holds private & public keys.
- Transaction Data: Sender, recipient, amount, timestamp.
- Hash Function: SHA-256 or Keccak-256.
- Digital Signature Algorithm (DSA/ECDSA/RSA): Generates signature.
- Blockchain Nodes: Verify transaction signatures.
Internal Workflow
[Transaction Data]
|
v
[Hashing Function] ----> [Hash Value]
|
v
[Private Key Signing] ----> [Digital Signature]
|
v
[Send to Network Nodes]
|
v
[Nodes Verify Signature Using Public Key]
|
[Transaction Validated & Added to Blockchain]
Diagram Explanation:
- Transaction is hashed to get a fixed-length fingerprint.
- The hash is signed using the sender’s private key.
- Nodes use the sender’s public key to verify authenticity without revealing the private key.
- Once verified, the transaction is appended to a block and distributed across the blockchain.
Integration Points with CI/CD or Cloud Tools
- Smart Contract Deployment: Sign contracts with digital signatures to ensure integrity.
- Blockchain APIs: Verify transactions programmatically.
- Cloud-based Wallets: Use secure key storage and signature verification.
- CI/CD pipelines for DApps: Automated testing of transactions’ signature validity.
4. Installation & Getting Started
Prerequisites
- Programming language: Python, JavaScript, or Go
- Blockchain framework: Ethereum, Bitcoin
- Libraries:
ecdsa,hashlibfor Python;cryptofor Node.js
Hands-on: Step-by-Step Guide (Python Example)
Step 1: Install required packages
pip install ecdsa
Step 2: Generate private and public keys
from ecdsa import SigningKey, SECP256k1
# Generate private key
private_key = SigningKey.generate(curve=SECP256k1)
print("Private Key:", private_key.to_string().hex())
# Generate public key
public_key = private_key.get_verifying_key()
print("Public Key:", public_key.to_string().hex())
Step 3: Sign transaction data
import hashlib
transaction = "Send 5 BTC from Alice to Bob"
transaction_hash = hashlib.sha256(transaction.encode()).digest()
signature = private_key.sign(transaction_hash)
print("Digital Signature:", signature.hex())
Step 4: Verify signature
is_valid = public_key.verify(signature, transaction_hash)
print("Signature valid?", is_valid)
5. Real-World Use Cases
- Bitcoin Transactions
- Uses ECDSA (Elliptic Curve Digital Signature Algorithm)
- Every transaction is signed by the sender’s private key.
- Ethereum Smart Contracts
- Sign messages off-chain to authorize actions on-chain.
- Example:
eth_signRPC method.
- Hyperledger Fabric
- Transaction proposals are signed by clients and validated by peers.
- NFT Ownership Transfer
- Digital signatures verify authenticity of ownership transfers.
6. Benefits & Limitations
Key Advantages
- Ensures transaction authenticity.
- Provides non-repudiation.
- Lightweight and fast in blockchain networks.
- Eliminates need for centralized trust.
Common Challenges
- Key management is critical; losing a private key means losing access.
- Quantum computing could potentially break current algorithms.
- Signature verification requires computational resources.
7. Best Practices & Recommendations
- Use strong algorithms: ECDSA, EdDSA
- Protect private keys: Hardware wallets, cold storage.
- Regularly update libraries: Avoid vulnerabilities.
- Monitor signature verification times: Ensure network performance.
Automation Ideas
- Integrate signature validation into CI/CD pipelines.
- Automatically alert on failed verification attempts.
8. Comparison with Alternatives
| Feature | Digital Signature | Password-based Authentication | Multi-factor Authentication |
|---|---|---|---|
| Non-repudiation | ✅ | ❌ | ✅ (partially) |
| Key Management | Private/Public keys | User memory | Private/Public keys + OTP |
| Integrity | ✅ | ❌ | ✅ |
| Scalability | ✅ (fast verification) | ❌ | Moderate |
| Suitability for blockchain | ✅ | ❌ | Limited |
When to choose Digital Signature:
- Blockchain or cryptoblockcoin transactions.
- Any decentralized, trustless environment.
- Scenarios requiring non-repudiation and integrity.
9. Conclusion
Key Takeaways
- Digital signatures are essential in cryptoblockcoins for trustless, secure transactions.
- They ensure authenticity, integrity, and non-repudiation.
- Implementation requires secure key management and adherence to best practices.
- Future trends include post-quantum cryptography and faster signature algorithms.
Next Steps
- Explore advanced algorithms like EdDSA, Schnorr signatures.
- Implement digital signatures in smart contracts.
- Monitor emerging quantum-resistant cryptographic standards.
Official Docs & Communities
- Bitcoin Developer Documentation
- Ethereum Signature Docs
- Hyperledger Fabric Docs
- StackExchange Cryptography
Category: