1. Introduction & Overview
What is Encryption?
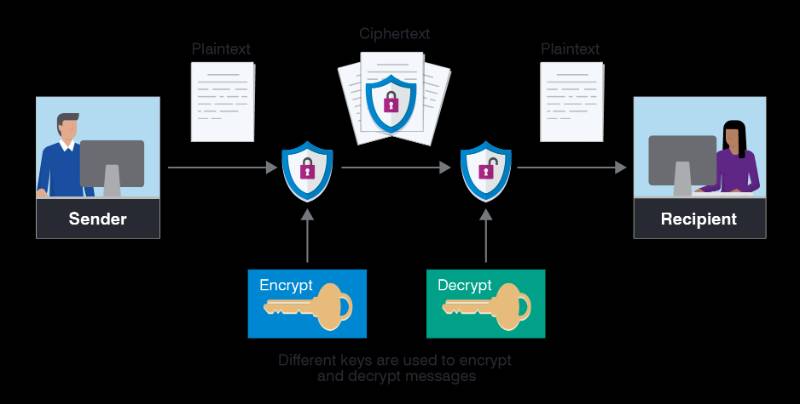
Encryption is the process of transforming readable data (plaintext) into an unreadable format (ciphertext) using mathematical algorithms and keys. Only authorized parties with the correct decryption key can revert it back to the original data.
In simpler terms, encryption is like locking your digital data in a safe, where only someone with the right combination can open it.
History or Background
- Ancient Cryptography: Caesar Cipher (~58 BC) – simple letter shift.
- Modern Cryptography: 1970s – development of symmetric and asymmetric algorithms.
- Digital Encryption: AES (Advanced Encryption Standard) adopted in 2001.
- Blockchain Era: With Bitcoin in 2009, encryption became fundamental for secure transactions.
Why Encryption is Relevant in Cryptoblockcoins
- Transaction Security: Ensures that transaction details are confidential.
- Wallet Protection: Protects private keys from unauthorized access.
- Network Integrity: Prevents double-spending and fraudulent transactions.
- Decentralized Trust: Builds trust without relying on centralized authorities.
2. Core Concepts & Terminology
| Term | Definition | Relevance in Cryptoblockcoins |
|---|---|---|
| Plaintext | Original readable data | Transaction information before encryption |
| Ciphertext | Encrypted, unreadable data | Stored or transmitted securely in blockchain |
| Symmetric Encryption | Same key used for encryption & decryption | Used in private blockchain channels |
| Asymmetric Encryption | Public & private key pair | Used for wallet addresses and signing transactions |
| Hashing | One-way encryption | Verifies data integrity in blocks |
| Digital Signature | Encrypted hash with private key | Validates sender & prevents tampering |
| Key Pair | Combination of private & public key | Wallet ownership & transaction verification |
| Nonce | Random number in block mining | Prevents replay attacks |
How Encryption Fits into Cryptoblockcoins Lifecycle
- Wallet Creation: Encryption generates key pairs.
- Transaction Signing: Private key encrypts the transaction hash.
- Block Validation: Miners verify encrypted signatures.
- Ledger Recording: Transactions are stored immutably, secured by hashes and encryption.
3. Architecture & How It Works
Components of Encryption in Blockchain
- Wallets – Store keys securely.
- Transaction Module – Prepares data for encryption.
- Encryption Algorithms – Symmetric (AES), Asymmetric (RSA, ECC).
- Digital Signature Module – Signs transactions.
- Verification Nodes – Validate transactions by decrypting signatures.
- Blockchain Ledger – Stores encrypted and hashed transaction blocks.
Internal Workflow
- Step 1: User initiates a transaction → plaintext transaction data.
- Step 2: Transaction hashed → unique fingerprint.
- Step 3: Private key signs the hash → digital signature.
- Step 4: Transaction + signature broadcast to network nodes.
- Step 5: Nodes verify using sender’s public key.
- Step 6: Valid transaction added to block → encrypted hashes stored.
Architecture Diagram (Textual Description)
+--------------------+ +-------------------+
| User Wallet | | Transaction |
| (Private & Public) |-----> | Creation Module |
+--------------------+ +-------------------+
| |
v v
+----------------+ +--------------------+
| Digital Signer | | Encryption Engine |
+----------------+ +--------------------+
| |
v v
+-------------------------------------------+
| Blockchain Network Nodes |
| - Verify Signature |
| - Validate Transaction Hash |
| - Consensus Protocol (PoW/PoS) |
+-------------------------------------------+
|
v
+------------------+
| Ledger (Blocks) |
| - Encrypted Data |
| - Hash Chain |
+------------------+
Integration Points with CI/CD or Cloud Tools
- CI/CD: Automated testing for smart contract encryption modules.
- Cloud: Cloud Key Management Services (AWS KMS, Azure Key Vault) for wallet backup and encryption key rotation.
- Monitoring Tools: Verify encryption compliance and key usage logs.
4. Installation & Getting Started
Basic Setup / Prerequisites
- Node.js or Python environment
- Cryptography library (
pycryptodomefor Python) - Blockchain client (e.g., Bitcoin Core or Ethereum node)
- Basic understanding of keys & transactions
Hands-on: Beginner-Friendly Example
Python Example: Asymmetric Encryption with RSA
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
from Crypto.Random import get_random_bytes
# Generate RSA key pair
key = RSA.generate(2048)
private_key = key.export_key()
public_key = key.publickey().export_key()
# Encrypt data
cipher = PKCS1_OAEP.new(RSA.import_key(public_key))
plaintext = b'Transaction Data'
ciphertext = cipher.encrypt(plaintext)
# Decrypt data
decipher = PKCS1_OAEP.new(RSA.import_key(private_key))
decrypted = decipher.decrypt(ciphertext)
print("Original:", plaintext)
print("Encrypted:", ciphertext)
print("Decrypted:", decrypted)
Output Table: Encryption Steps
| Step | Description | Code Reference |
|---|---|---|
| Key Generation | Generate public & private keys | RSA.generate(2048) |
| Encryption | Convert plaintext to ciphertext | cipher.encrypt() |
| Decryption | Recover plaintext from ciphertext | decipher.decrypt() |
5. Real-World Use Cases
Cryptoblockcoins Scenarios
- Bitcoin Transactions
- Uses ECDSA (Elliptic Curve Digital Signature Algorithm)
- Encrypts transaction data and signs with private key.
- Ethereum Smart Contracts
- Uses encryption for private key signatures.
- Ensures immutable execution of smart contracts.
- Privacy Coins (Monero, ZCash)
- Uses advanced cryptography (Ring Signatures, zk-SNARKS)
- Hides transaction amounts and sender/receiver identity.
- Decentralized Exchanges
- Encrypts wallet keys and transaction data in smart contracts.
6. Benefits & Limitations
Key Advantages
- Secures sensitive data.
- Prevents fraud and unauthorized access.
- Ensures integrity of blockchain ledger.
- Enables trustless transactions.
Common Challenges
- Key management complexity.
- Performance overhead for large-scale transactions.
- Quantum computing threats to asymmetric encryption.
- Compliance & legal constraints for encrypted data storage.
7. Best Practices & Recommendations
| Area | Recommendation |
|---|---|
| Key Management | Rotate keys periodically; use secure hardware wallets |
| Algorithm Choice | Use AES-256 for symmetric, ECC for asymmetric |
| Digital Signatures | Always sign transaction hash, not raw data |
| Storage | Encrypted backup for private keys |
| Automation | Integrate encryption testing in CI/CD |
| Compliance | Align with GDPR, ISO 27001, local regulations |
Security Tips
- Never share private keys.
- Use multi-factor authentication.
- Implement anti-tamper mechanisms in wallets.
Performance & Maintenance
- Monitor encryption CPU usage.
- Optimize transaction signing for bulk operations.
- Schedule regular audits for blockchain nodes.
8. Comparison with Alternatives
| Encryption Type | Speed | Security | Use Case |
|---|---|---|---|
| Symmetric (AES) | Fast | High | Private blockchains, data storage |
| Asymmetric (RSA/ECC) | Moderate | Very High | Wallet keys, public transaction verification |
| Hash Functions | Very Fast | One-way | Block integrity verification |
When to Choose Encryption
- For protecting sensitive wallet data.
- For transaction signing in public networks.
- For privacy-oriented applications like Monero/ZCash.
9. Conclusion
Final Thoughts
Encryption is the backbone of cryptoblockcoin security. It ensures data integrity, user privacy, and trustless decentralized systems. As blockchain scales, advanced encryption methods will continue to evolve to counter new threats.
Future Trends
- Post-quantum encryption algorithms.
- Zero-knowledge proofs for privacy.
- Hardware-based encryption for wallets.
- Cloud-native encrypted blockchain deployments.
Next Steps
- Experiment with Python/Node.js encryption libraries.
- Deploy a small blockchain testnet.
- Implement and test asymmetric encryption in transactions.
- Explore privacy coins for advanced cryptography techniques.
Official Docs & Communities
- Bitcoin Developer Guide – Security
- Ethereum Docs – Cryptography
- PyCryptodome Documentation
- StackExchange Cryptography