1. Introduction & Overview
What is a Merkle Tree?
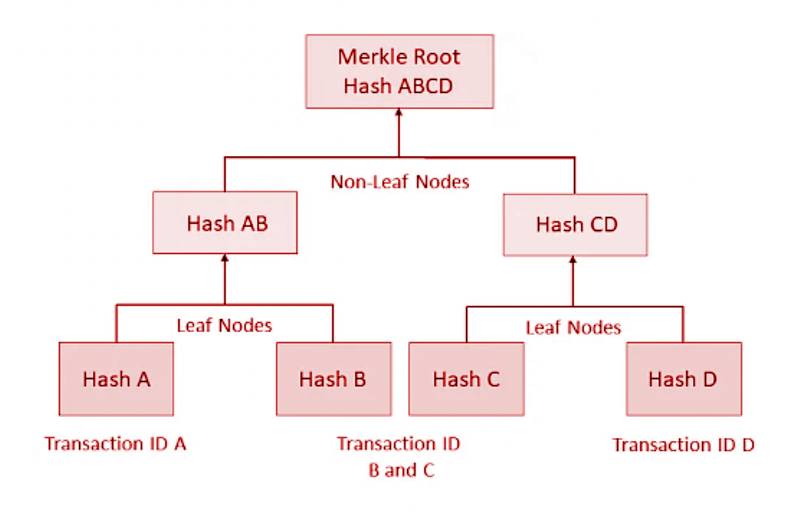
A Merkle Tree (or hash tree) is a data structure used to efficiently and securely verify the contents of large datasets. It works by repeatedly hashing pairs of data until a single root hash (Merkle Root) is obtained.
- The leaf nodes contain the hash of the data blocks.
- The intermediate nodes contain hashes of their child nodes.
- The root node summarizes all underlying data.
Merkle Trees are crucial in blockchain systems because they enable quick verification of data integrity without downloading the entire dataset.
Key benefits:
- Efficient data verification
- Tamper-proof data integrity
- Scalability for large datasets
History / Background
- Introduced by Ralph Merkle in 1979.
- Originally proposed for secure and efficient authentication of data.
- Adopted in cryptocurrencies like Bitcoin (2008) and Ethereum for transaction verification and block integrity.
Why it is Relevant in Cryptoblockcoins
- Cryptoblockcoins deal with distributed ledgers, where every node needs to verify transactions efficiently.
- Merkle Trees allow lightweight clients to verify the inclusion of transactions without downloading the entire blockchain.
- Used in:
- Bitcoin: For validating transaction inclusion in blocks.
- Ethereum: For state verification in the Ethereum Virtual Machine (EVM).
- Provides security guarantees: Any tampering in data leads to Merkle Root mismatch.
2. Core Concepts & Terminology
| Term | Definition |
|---|---|
| Leaf Node | Hash of individual data block or transaction. |
| Non-Leaf Node | Hash of concatenated child hashes. |
| Merkle Root | Top-most hash representing the entire tree. |
| Proof of Inclusion (Merkle Proof) | A sequence of hashes to verify that a leaf is part of the tree. |
| Hash Function | Cryptographic function (SHA-256, Keccak-256) used for hashing nodes. |
| Binary Tree | Each node has at most two children; common Merkle Tree structure. |
How it fits in Cryptoblockcoins Lifecycle
- Transactions are created and collected into a block.
- Each transaction is hashed to form leaf nodes.
- Hashes are paired and combined recursively to form non-leaf nodes.
- The top hash is stored as Merkle Root in the block header.
- Light clients can request Merkle Proof to validate transaction inclusion.
3. Architecture & How It Works
Components
- Transaction / Data Blocks: Raw data or transactions.
- Leaf Hashes: SHA-256 or Keccak-256 of each transaction.
- Intermediate Nodes: Hashes of concatenated child hashes.
- Merkle Root: Single hash representing the block.
- Merkle Proof: Minimal set of sibling hashes to verify inclusion.
Internal Workflow
- Collect transactions (Tx1, Tx2, … TxN)
- Compute leaf hashes: H1 = hash(Tx1), H2 = hash(Tx2), …
- Combine pairs: H12 = hash(H1 || H2)
- Repeat until single Merkle Root is computed.
- Store Merkle Root in block header.
Architecture Diagram
Merkle Root
|
---------------------
| |
Hash12 Hash34
/ \ / \
Hash1 Hash2 Hash3 Hash4
| | | |
Tx1 Tx2 Tx3 Tx4
- Tx1–Tx4: Raw transactions
- Hash1–Hash4: Leaf node hashes
- Hash12, Hash34: Non-leaf hashes
- Merkle Root: Root hash for the block
Note: For odd number of transactions, the last hash is duplicated to maintain a balanced tree.
Integration Points
- Blockchain Clients: Bitcoin Core, Ethereum Geth, Hyperledger Fabric.
- CI/CD Pipelines: Validate blockchain code and transaction processing.
- Cloud Tools: AWS Managed Blockchain, Azure Blockchain Service, for verifying transaction integrity at scale.
4. Installation & Getting Started
Prerequisites
- Programming language (Python, Go, JavaScript)
- Cryptography library for hash functions
- Sample transaction data
Hands-On: Python Example
import hashlib
def hash_pair(a, b):
return hashlib.sha256((a + b).encode()).hexdigest()
# Sample transactions
transactions = ["Tx1", "Tx2", "Tx3", "Tx4"]
# Compute leaf hashes
leaf_hashes = [hashlib.sha256(tx.encode()).hexdigest() for tx in transactions]
# Compute next level hashes
level1 = [hash_pair(leaf_hashes[i], leaf_hashes[i+1]) for i in range(0, len(leaf_hashes), 2)]
# Compute Merkle Root
merkle_root = hash_pair(level1[0], level1[1])
print("Merkle Root:", merkle_root)
Output: A single hash representing the Merkle Root.
5. Real-World Use Cases
| Blockchain | Use Case | Details |
|---|---|---|
| Bitcoin | Transaction Verification | SPV clients can verify transactions with Merkle Proof. |
| Ethereum | State Verification | Ethereum uses Patricia Merkle Trees to track account states. |
| Hyperledger | Auditing & Compliance | Used in permissioned blockchains to validate transactions. |
| Filecoin / IPFS | Data Integrity | Ensures files are untampered and retrievable. |
Industry-specific example:
- Supply Chain: Merkle Trees allow verification of product authenticity without revealing full transaction history.
- Finance: Banks can verify ledger updates efficiently for auditing purposes.
6. Benefits & Limitations
Advantages
- Fast verification (O(log n) time)
- Tamper-evident
- Supports lightweight clients
- Efficient storage (only hashes stored, not full data)
Limitations
- Cannot recover corrupted data, only detect it
- Requires tree balancing for uneven datasets
- Single hash function vulnerability affects all nodes
7. Best Practices & Recommendations
| Area | Recommendation |
|---|---|
| Security | Use secure hash functions (SHA-256, SHA-3) |
| Performance | Build balanced trees; batch transactions efficiently |
| Maintenance | Recompute only affected branches on data update |
| Compliance | Log Merkle Roots for audit trails |
Automation Ideas:
- CI/CD scripts for verifying block integrity
- Scheduled tree recomputation for high-transaction systems
8. Comparison with Alternatives
| Tool | Use Case | Pros | Cons |
|---|---|---|---|
| Merkle Tree | Transaction validation | Efficient, scalable, lightweight | Single hash function dependency |
| Hash List | Simple data verification | Easy to implement | O(n) verification, not scalable |
| Patricia Trie | Ethereum state | Compact, fast key lookup | More complex, higher memory usage |
When to choose Merkle Tree:
- Use when transaction verification and lightweight proof are needed.
- Avoid for full key-value state mapping; consider Patricia Trie instead.
9. Conclusion
- Merkle Trees are a fundamental building block in blockchain technology.
- Enable efficient verification, security, and scalability for cryptoblockcoins.
- Essential for light clients, auditing, and compliance in distributed ledgers.
- Future trends:
- Integration with zero-knowledge proofs for privacy.
- Optimized hash functions for quantum resistance.
- Hybrid Merkle Trees for IoT and microtransactions.
Category: