1. Introduction & Overview
What is a Public Key?
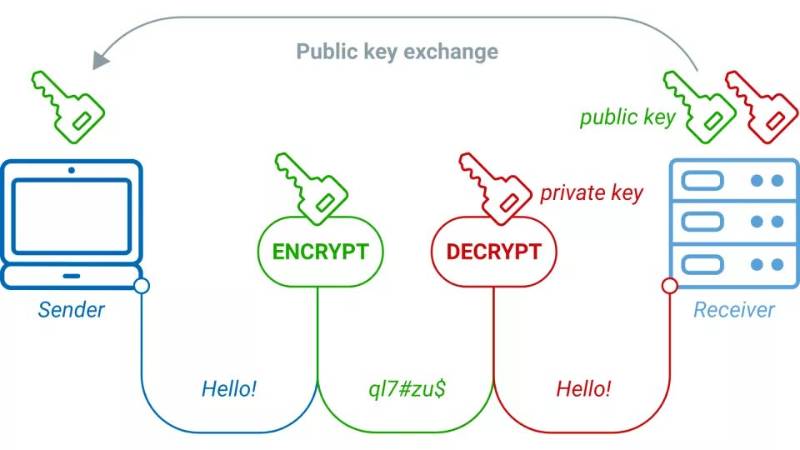
A Public Key is a cryptographic code that allows users to receive funds in blockchain-based systems. In public-key cryptography (asymmetric cryptography), each user has:
- Private Key: Kept secret; used to sign transactions.
- Public Key: Shared with the world; used to receive funds or verify signatures.
In cryptoblockcoins like Bitcoin or Ethereum:
- The public key derives the wallet address.
- Public keys ensure secure transactions without revealing private keys.
History / Background
- 1970s: Introduction of asymmetric cryptography by Diffie-Hellman (1976) and RSA (1978).
- 2008: Bitcoin’s whitepaper by Satoshi Nakamoto introduced public/private key pairs for secure, peer-to-peer digital cash.
- Present: Used in most blockchain-based cryptos for identity verification, transactions, and smart contract interactions.
Relevance in Cryptoblockcoins
- Enables trustless transactions: Senders can verify ownership without central authority.
- Provides digital signatures for integrity.
- Essential for wallet security and transaction validation.
2. Core Concepts & Terminology
| Term | Definition | Relevance in Cryptoblockcoins |
|---|---|---|
| Public Key | Cryptographic key shared publicly to receive funds or verify signatures | Used to generate wallet addresses and verify transactions |
| Private Key | Secret cryptographic key used to sign transactions | Must remain confidential; proves ownership |
| Address | Shortened hash of public key | Used for sending/receiving funds |
| Digital Signature | Mathematical proof linking a transaction to a private key | Verifies authenticity and prevents tampering |
| Asymmetric Cryptography | Encryption technique using public/private key pair | Core security mechanism in blockchain |
| ECDSA (Elliptic Curve Digital Signature Algorithm) | Cryptographic algorithm used in Bitcoin | Efficient and secure key generation and signing |
Public Key in Cryptoblockcoin Lifecycle
- Key Generation: Wallet generates public/private key pair.
- Address Derivation: Public key is hashed to form wallet address.
- Transaction Signing: Private key signs transaction; public key verifies.
- Verification: Network nodes use public key to confirm authenticity.
3. Architecture & How It Works
Components & Workflow
Key Components:
- Wallet/Client: Generates key pair.
- Blockchain Node: Validates transactions.
- Transaction Pool: Broadcasts signed transactions.
- Mining/Consensus Layer: Confirms transactions on the blockchain.
Internal Workflow:
- User generates a public/private key pair.
- Public key is shared; private key remains secret.
- User signs a transaction with the private key.
- Network nodes verify using the public key.
- Verified transaction is added to the blockchain.
Architecture Diagram
Since I can’t draw, here’s a descriptive diagram:
+-------------------+ +-----------------+ +-------------------+
| User Wallet | | Blockchain Node | | Blockchain Ledger|
|-------------------| |----------------| |-------------------|
| Generate Key Pair |-----> | Validate TX |-----> | Store TX |
| Public Key shared | | Verify Signature| | Immutable Ledger |
| Private Key secret | +-----------------+ +-------------------+
+-------------------+
Flow:
- Key Generation → Transaction Signing → Verification → Ledger Storage
Integration Points with CI/CD or Cloud Tools
- Wallet software can be versioned and deployed via CI/CD pipelines.
- Public keys are used for secure API interactions or smart contract deployment.
- Cloud-managed blockchain nodes rely on public keys for authentication and encryption.
4. Installation & Getting Started
Basic Setup / Prerequisites
- Programming Language: Python, Node.js, or Go.
- Libraries:
ecdsa,bitcoinlib(Python),ethers.js(Node.js) - Development Environment: Any IDE + Node/Python runtime.
Hands-On: Generate Public Key (Python Example)
from ecdsa import SigningKey, SECP256k1
# Generate private key
private_key = SigningKey.generate(curve=SECP256k1)
print(f"Private Key: {private_key.to_string().hex()}")
# Generate public key
public_key = private_key.verifying_key
print(f"Public Key: {public_key.to_string().hex()}")
Output Example:
Private Key: 5f1b6e9c6a1e5f42f...
Public Key: 0431a6f7c5b8...
Hands-On: Generate Wallet Address (Bitcoin Example)
import hashlib
import base58
pub_key_bytes = public_key.to_string()
sha256 = hashlib.sha256(pub_key_bytes).digest()
ripemd160 = hashlib.new('ripemd160', sha256).digest()
address = base58.b58encode_check(b'\x00' + ripemd160)
print(f"Wallet Address: {address.decode()}")
5. Real-World Use Cases
| Use Case | Description | Example Cryptoblockcoins |
|---|---|---|
| Wallet Address Generation | Public keys derive wallet addresses | Bitcoin, Ethereum, Litecoin |
| Transaction Verification | Nodes verify signature using public key | Bitcoin (BTC), Ethereum (ETH) |
| Smart Contract Interaction | Public keys used for signing transactions | Ethereum, Solana, Cardano |
| Multi-Signature Wallets | Multiple public keys authorize single transaction | Bitcoin MultiSig, Ethereum Gnosis Safe |
Industry-Specific Examples:
- Finance: Banks experimenting with blockchain for cross-border payments use public/private key infrastructure.
- Supply Chain: Public keys verify authenticity of recorded product data.
- Healthcare: Patient data encryption and verification using blockchain-based public keys.
6. Benefits & Limitations
Key Advantages
- Security without central authority.
- Non-repudiation: Transactions cannot be denied.
- Privacy: Public key does not reveal private key.
Challenges / Limitations
- Losing the private key = losing access to funds.
- Key management complexity for businesses.
- Computational overhead in key generation and verification.
Best Practices & Recommendations
- Use hardware wallets for storing private keys.
- Backup private keys securely.
- Rotate keys periodically in enterprise blockchain systems.
- Use libraries with proven cryptographic algorithms (ECDSA, EdDSA).
7. Best Practices & Recommendations
Security Tips
- Secure Key Storage: Use hardware wallets (e.g., Ledger, Trezor) or cloud HSMs to store private keys.
- Multi-Signature Wallets: Require multiple signatures for transactions to enhance security.
- Regular Audits: Audit smart contracts and wallet software for vulnerabilities.
Performance
- Optimize Algorithms: Use ECC (e.g., SECP256k1) for faster key generation and signing.
- Batch Processing: Group transactions to reduce the number of signature operations.
Maintenance
- Key Rotation: Periodically generate new key pairs to mitigate risks.
- Backup Keys: Store private key backups in secure, offline locations.
Compliance Alignment
- KYC/AML: Integrate with KYC/AML systems for regulatory compliance in financial applications.
- Privacy Standards: Use zero-knowledge proofs for enhanced privacy where required (e.g., GDPR compliance).
Automation Ideas
- CI/CD Pipelines: Automate key generation and testing in development environments.
- Monitoring: Implement blockchain explorers to monitor transaction validity and network health.
8. Comparison with Alternatives
| Feature | Public Key Cryptography | Symmetric Key Cryptography |
|---|---|---|
| Key Type | Public/Private Pair | Single Shared Key |
| Security | High, private key secret | Moderate, shared key risk |
| Transaction Verification | Yes, digital signatures | No |
| Use in Blockchain | Essential | Rarely used |
When to Use Public Key Over Others:
- When secure, decentralized verification is needed.
- In any cryptoblockcoin transaction system.
- For smart contract deployments.
9. Conclusion
Final Thoughts
Public keys are the backbone of blockchain security, enabling trustless, verifiable transactions. They:
- Securely link users to transactions.
- Allow for decentralized verification.
- Serve as foundational elements in wallet and blockchain architecture.
Future Trends
- Quantum-resistant public key algorithms (e.g., lattice-based cryptography)
- Integration in IoT devices for blockchain-based authentication
- Increased adoption in DeFi and enterprise blockchain solutions
Next Steps
- Practice generating public/private keys in Python or Node.js.
- Understand transaction signing and verification.
- Explore multi-signature wallets and smart contract interactions.
- Stay updated on cryptography advancements (post-quantum, EdDSA).
Official Documentation & Communities:
- Bitcoin Developer Guide
- Ethereum Public Key Management
- Stack Exchange – Bitcoin
- CryptoDev Reddit Communities
Category: