1. Introduction & Overview
1.1 What is SHA-256?
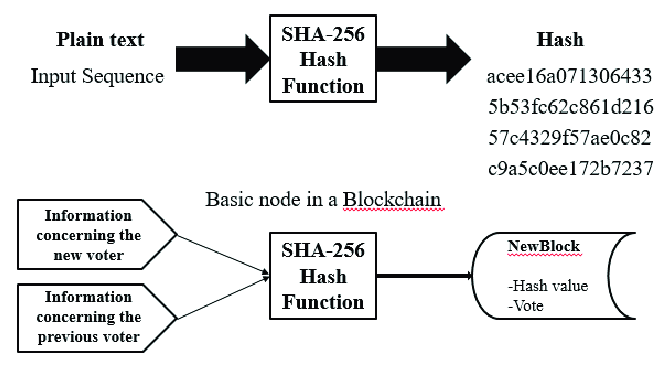
SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function that converts any input data into a fixed-length 256-bit (32-byte) string of characters.
Key properties of SHA-256:
- Deterministic: Same input always produces the same hash.
- Irreversible: Cannot retrieve original data from the hash.
- Collision-resistant: Extremely unlikely for two different inputs to produce the same hash.
- Fast computation: Efficiently generates hashes for large data.
- Avalanche effect: Small changes in input produce vastly different outputs.
Example:
import hashlib
data = "Hello, Blockchain!"
hash_object = hashlib.sha256(data.encode())
print(hash_object.hexdigest())
Output:
a3f5e1b6b0b7c9a... (64 hex characters)
1.2 History or Background
- SHA-256 is part of the SHA-2 family, designed by the National Security Agency (NSA) in 2001.
- SHA-2 replaced SHA-1 due to security vulnerabilities in SHA-1.
- Widely used in digital signatures, certificate validation, and blockchain systems.
1.3 Why is SHA-256 relevant in cryptoblockcoins?
- SHA-256 is the backbone of blockchain integrity.
- Provides secure hashing for:
- Mining (Proof-of-Work): Hashing block headers to meet difficulty targets.
- Transaction verification: Ensuring data immutability.
- Wallet address generation: Hashing public keys to derive addresses.
- Powers the security model of Bitcoin and many other cryptocurrencies.
2. Core Concepts & Terminology
| Term | Definition |
|---|---|
| Hash Function | A function that converts data of any size to a fixed-size hash. |
| Collision | Two inputs producing the same hash value (undesirable). |
| Pre-image Resistance | Difficulty in reversing the hash to find original input. |
| Block Header | Metadata of a blockchain block including timestamp, previous hash, merkle root. |
| Merkle Tree | Tree structure for hashing transactions for integrity and efficient verification. |
| Proof-of-Work (PoW) | Mining process involving finding a nonce that satisfies SHA-256 difficulty target. |
Lifecycle in Cryptoblockcoins:
- Transactions are grouped into a block.
- Each transaction is hashed.
- Transaction hashes form a Merkle tree, root stored in the block header.
- SHA-256 applied to block headers for mining.
- New blocks added to the blockchain after valid hash found.
3. Architecture & How It Works
3.1 Components & Internal Workflow
SHA-256 Workflow (Step-by-Step):
- Preprocessing
- Padding the message to make its length a multiple of 512 bits.
- Append message length in bits at the end.
- Message Parsing
- Divide the padded message into 512-bit blocks.
- Message Expansion
- Each block is expanded into 64 32-bit words.
- Compression Function
- Uses 64 rounds of processing with constants and bitwise operations.
- Final Hash Computation
- Combines intermediate hash values to produce a 256-bit output.
3.2 Architecture Diagram
+---------------------------+
| Input Message |
+---------------------------+
|
v
+---------------------------+
| Preprocessing |
| - Padding |
| - Append length |
+---------------------------+
|
v
+---------------------------+
| Message Parsing |
| - 512-bit blocks |
+---------------------------+
|
v
+---------------------------+
| Message Expansion |
| - 64 32-bit words |
+---------------------------+
|
v
+---------------------------+
| Compression Function |
| - 64 rounds of bitwise |
| operations & constants |
+---------------------------+
|
v
+---------------------------+
| Output Hash (256-bit) |
+---------------------------+
3.3 Integration Points with CI/CD or Cloud Tools
- CI/CD pipelines: Automatically hash transaction data or log files.
- Cloud storage: SHA-256 hashes verify integrity of data uploads/downloads.
- Blockchain nodes: SHA-256 validates block and transaction integrity before propagation.
4. Installation & Getting Started
4.1 Basic Setup / Prerequisites
- Python 3.x installed
hashliblibrary (built-in)- Optional: Node.js (
cryptomodule) for JavaScript-based development
4.2 Step-by-Step Beginner-Friendly Guide
Python Example:
import hashlib
# Step 1: Define input
data = "Transaction data for block"
# Step 2: Convert to bytes
data_bytes = data.encode()
# Step 3: Generate SHA-256 hash
sha256_hash = hashlib.sha256(data_bytes).hexdigest()
# Step 4: Output hash
print("SHA-256 Hash:", sha256_hash)
Node.js Example:
const crypto = require('crypto');
let data = "Transaction data for block";
let hash = crypto.createHash('sha256').update(data).digest('hex');
console.log("SHA-256 Hash:", hash);
5. Real-World Use Cases
5.1 Cryptoblockcoin Scenarios
- Bitcoin Mining
- Miners hash block headers to find a nonce that meets difficulty target.
- Ethereum Transaction Verification
- SHA-256 used in Ethereum’s transaction and Merkle Patricia trees.
- Digital Wallet Addresses
- Public keys hashed with SHA-256 and RIPEMD-160 to generate addresses.
- Proof-of-Work Systems
- Any PoW-based cryptocurrency relies on SHA-256 for securing mining puzzles.
Industry-specific Applications
- Supply chain: Tracking shipment authenticity using blockchain and SHA-256 hashes.
- Financial sector: Immutable audit trails via hashed transactions.
- IoT: Device data hashed and recorded on blockchain for security.
6. Benefits & Limitations
6.1 Key Advantages
- Extremely secure against pre-image and collision attacks.
- Efficient for mining and transaction verification.
- Widely adopted and trusted in industry standards.
- Supports decentralization and immutability in blockchain systems.
6.2 Challenges & Limitations
| Challenge | Explanation |
|---|---|
| Quantum Vulnerability | SHA-256 may be at risk with future quantum computers. |
| Energy-intensive Mining | PoW using SHA-256 consumes large energy. |
| No Built-in Encryption | Only a hash function; cannot encrypt or hide data content. |
7. Best Practices & Recommendations
- Always use latest SHA-2 standards.
- Verify hashes after transmission to prevent tampering.
- For blockchain development:
- Combine SHA-256 with Merkle trees.
- Ensure proper nonce selection in mining.
- Automate hash verification in CI/CD pipelines for data integrity.
- Maintain compliance with ISO/IEC 10118-3 and other cryptographic standards.
8. Comparison with Alternatives
| Hash Algorithm | Output Size | Collision Resistance | Speed | Use Cases |
|---|---|---|---|---|
| SHA-1 | 160-bit | Weak | Fast | Legacy systems |
| SHA-256 | 256-bit | Strong | Moderate | Bitcoin, Blockchain |
| SHA-512 | 512-bit | Very Strong | Moderate | High-security systems |
| Blake2b | Variable | Very Strong | Fast | File integrity, cryptocurrency |
When to choose SHA-256:
- Blockchain PoW-based systems.
- Secure transaction verification.
- Platforms where SHA-2 is industry-standard (Bitcoin, Litecoin).
9. Conclusion
- SHA-256 is a critical building block of modern cryptoblockcoins.
- It provides security, immutability, and trust in decentralized networks.
- Developers and organizations should follow best practices for integration, performance optimization, and future-proofing against emerging threats.
- Future trends:
- Quantum-resistant hashing.
- Integration with layer 2 scaling solutions.
- Automated hash verification in enterprise blockchain ecosystems.
References & Resources:
- NIST FIPS 180-4
- Bitcoin Whitepaper
- Python hashlib Documentation
- Node.js Crypto Module
Category: